Published on 28 Nov 2023.
Via SSH, also known as Secure Shell, is a protocol for managing machines securely over the Internet. It has been the preferred way of managing Unix machines for years, and is now available for Windows.
Users can simply log in using their username and password. But there's also a more secure and practical solution: SSH key authentication.
SSH at Kinamo
As a managed service provider, Kinamo has to deal with server management on a daily basis, both for in-house machines and for the cloud servers we manage for our customers. The number of times a server is connected is almost impossible to track.
So it's important to be able to do so securely. This isn't always easy, as servers - just like an application or other device - often wait for a username and password to be entered.
Passing on passwords, providing authentication data to customers, third parties, etc. is a thorny security issue, and is also a weak link in the overall security chain.
That's why we'd like to introduce you to an authentication method that we think is very popular on the servers we manage!
Advantages of SSH
Working with an SSH key offers a number of advantages:
- No need to send a password.
- Password login" can be disabled on the server. This is a perfect solution to counter so-called "brute force" attacks.
- You can use your own key on different servers. So you don't need to keep a list of passwords.
- Your public key can be shared with other people without any problem. They can install this public key on a server and give you access to it. For example, we recommend that web developers who need to work on a client's server authenticate via an SSH key.
Anything that has advantages always has at least one disadvantage. The disadvantage is that your private SSH key is stored on disk.
If someone gets hold of this key, they can also access all the machines to which you have access.
It is therefore strongly recommended to protect this private key with a password. By using a key with a password, you immediately have two-factor authentication: your key and the password.
You can easily set the password when you create the key.
That's great, but how do you get started?
Creating a key
To create SSH keys, we use OpenSSH.
OpenSSH is - it's safe to say - in practice the default SSH client.
OpenSSH has always been available for Mac OS and Linux operating systems and has recently been available for Windows 10 and Windows Server 2019.
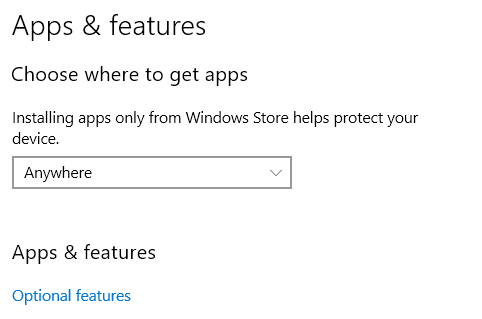
If you want to use SSH on a Windows operating system, you'll need to enable the "OpenSSH Client" feature.
You'll find it under "Apps > Apps and features > Optional features".

Mac OS and Linux users normally already have the SSH client on their system. You can test it with the following command:
ssh -V OpenSSH_9.2p1 Debian-2+deb12u5, OpenSSL 3.0.15 3 Sep 2024If OpenSSH is installed on your computer, creating your own SSH key is a simple process. You can do this with the ssh-keygen command.
You'll be asked where you want to store the key and what password you want to set.
To choose the default option, simply press Enter.
kinamo@debian:/$ ssh-keygen
Generate a public/private rsa key pair.
Enter the file in which you wish to save the key (/home/kinamo/.ssh/id_rsa):
Create directory '/home/kinamo/.ssh'.
Enter the passphrase (empty if no passphrase has been entered):
Enter the same passphrase again:
Your login has been saved in /home/kinamo/.ssh/id_rsa.
Your public key has been saved in /home/kinamo/.ssh/id_rsa.pub.
The key fingerprint is :
SHA256:D7IyqOyoO+G8QbjE5RoCAdhMsTVM5IZPvxRlTMCY/M4 kinamo@debian
The random key image is :
+---[RSA 2048]----+
|=+o*=+.++ |
|..o==..o. |.
|. o.+.. |
|+ o+ ... |
|...o= ..o+ S
|=.o. .E+ o |
|++. o o . |
|++. o |
|B*. |
+----[SHA256]-----+Once you've created the keys, you can install the public key on a machine.
In the output from ssh-keygen, you'll see "Your public key has been saved in /home/kinamo/.ssh/id_rsa.pub.".
This is where your public key can be found in the id_rsa.pub file
Open the file at this point with notepad or another text editor.
It should look like this
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC+qYhABkyQ39Bjdaw9Uscu5ca+9APZJyIcjz3fJZmhpTe2+AyIg3aj/la0iRrymMBd3l7x3FBmmaXfek52AS/jsRhTRDS5IQ/yNFocKjqDur36jByANFGOLVy6aHV2sXNXkVqF7UX9CgA2sxNIZd4K7qJte8lh5781zdMX3Vsdn0NyvXw30HmZfv79jhtgeEZe7ER6SCAEHJ5oAa3hiqClvU8f4Chy/NpsKmGIcloLBXBpV/nLSTcmw+8Rdk5R2ilO1Dl+6sz38FLTFBjigj++IvleF0W/tclqhFEneen0Jryb9zB43TmeZMAEfbnycCECywKO9/ok8F97urVbdGSFkinamo@debian
Installing your key
The easiest way to install your key on a machine is to use ssh-copy-id.
This program installs your key completely automatically.
You need to connect to the server once, using your password. In this example, we'll install our key on the remote_server server using the command ssh-copy-id kinamo@remote_server.
kinamo@debian:/$ ssh-copy-id kinamo@remote_server
/usr/bin/ssh-copy-id : INFO : Source of the key(s) to be installed: "/home/kinamo/.ssh/id_rsa.pub".
Authenticity of host 'remote_server (xx.xx.xx.xx)' cannot be established.
The ECDSA key fingerprint is SHA256:.xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.
Are you sure you want to continue logging in (yes/no)? yes
/usr/bin/ssh-copy-id : INFO : login attempt with new key(s), to filter out those already installed.
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you're asked now, it's to install the new key(s).
kinamo@remote_server password :
kinamo@debian:/$ ssh-copy-id kinamo@remote_server
/usr/bin/ssh-copy-id : INFO : Source of key(s) to be installed: "/home/kinamo/.ssh/id_rsa.pub".
/usr/bin/ssh-copy-id : INFO : connection attempt with new key(s), to filter out those already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you're asked now, it's to install the new key(s)
kinamo@remote_server password :
Number of keys added: 1
Now try connecting to the machine with : "ssh 'kinamo@remote_server'"
and check that only the keys you wanted have been added.If ssh-copy-id is not available on your system (unfortunately, for Windows users), you can also install the key manually.
You then connect to the server on which you wish to place your key via SSH. via SSH.
Once connected to the server, create a new folder in your home folder called .ssh containing the file authorised_keys.
Open this file with a text editor and place the contents of your id_rsa.pub file in it.
ssh kinamo@remote_server
kinamo@remote_server:~$ mkdir ~/.ssh
kinamo@remote_server:~$ vim ~/.ssh/authorized_keysOnce the key has been installed, you can log out.
When you log in again, you no longer need to enter your user password.
Bonus: disable "log in with password" function
If you can log in using your SSH key, you can take an extra step to secure your server. You can disable the "connect using password" option.
This way, brute-force attacks on your SSH server no longer stand a chance. It's definitely worth thinking about!
Open your SSH server configuration:
vim/etc/ssh/sshd_config
Look for the PasswordAuthentication option.
By default, it's in the comments and set to"yes".
Remove the option from the comments and set it to"no":
PasswordAuthentication no
Now restart the SSH service:
kinamo@remote_server:~$ sudo systemctl restart ssh
From now on, you can only connect to your server via your SSH key!



